6 Common Cybersecurity Challenges And How You Can Tackle Them
Constant digital innovation has brought new devices, applications, and interconnectivity to boost employee productivity, and business workflows. But these advancements have also piqued the interest of cybercriminals looking to steal sensitive customer and business data, hold organizations to ransom, and generally cause mayhem.
Therefore your cybersecurity must be well-prepared to deal with the array of threats cybercrime can unleash to disrupt your business operations, customer lives, and employee livelihoods. Below are 6 common challenges and the steps your business can take to tackle them.
1. Phishing attacks
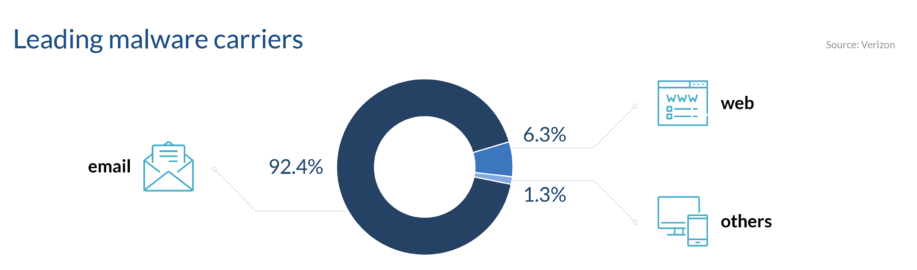
Phishing is a type of social engineering that attackers use to trick victims into giving up private information, such as passwords or sensitive data, and deploy malware on their systems.
The term originates from the word fish, as attackers fish for data. It happens through psychological manipulation and fraudulent communications, like emails, SMS messages, social media exploits, fake ads, and seemingly legitimate websites. Spoofing email addresses and phone numbers can make the messages look legitimate.
For instance, you might receive an email from your bank urgently requesting you change your password via the link in the email as your account may have become compromised in a data breach. The sender’s email address includes your bank domain, and the email looks legitimate. But, by entering your details via the provided link, you’re handing over your login credentials.
Through creating urgency, a phishing attacker can manipulate the most cautious person to overlook simple security procedures and do what the attacker wants. It can compromise business operations, bank details, sensitive customer data, trade secrets, and more.
Phishing is a well-established practice. Recent advancements in AI have added to its arsenal, making scams harder to detect. However, you can update your cybersecurity measures.

- Ensure security software and IT equipment is updated to avoid phishing malware attacks.
- Spelling and grammar errors in email addresses, URLs, websites, or content are hallmarks of phishing scams.
- Train employees not to panic with alarming emails or calls.
- Research and verify odd or suspicious communications, like data breaches or misspelled company names.
- Overconfidence is a phishing attacker’s dream trait as it makes people drop their guard. Ensure your employees know they’re fallible to scams.
- If you’ve fallen victim to a phishing scam, contact relevant authorities/departments immediately. Change any affected login credentials if you can via proper channels.
Phishing scams target a system difficult to guard, humans. So, train your employees to ask questions. For instance, researching what is .ae domain, if they’ve never heard of an AE domain before proceeding.
2. Ransomware
Ransomware is malware that locks/encrypts files preventing user access to a system. It asks for a ransom payment to decrypt the data and regain access. It can cost your business dearly in downtime, ransom payments, and data loss.
It’s often spread via phishing attacks, duping victims into installing malicious software. The result is helplessness as files are locked, and data is lost. Consider the following to prevent an attack and improve business security.
- Ensure up-to-date antivirus/anti-malware software on all devices.
- Only run authorized software. Avoid opening unauthorized software or files.
- Backup data regularly.
- Use phishing prevention to eliminate entry points.
- If an attack occurs, immediately disconnect devices from your network, notify cybersecurity teams, inform the authorities, and don’t pay the ransom as there’s no guarantee you’ll regain access.
3. Man in the middle attacks
A Man-In-The-Middle or MITM attack is when an attacker inserts themselves between two parties, allowing them to intercept communications, alter information, or conduct an attack. It could be when using a call transcription service, communicating with customers, or colleagues.
For instance, think about how you order takeout. You pick a restaurant, decide what you want, and place your order. The restaurant confirms your order, makes the food and sends it on its way.
If an attacker eavesdropped on your communication, they know what you’re ordering, where you’re ordering from, and where you live. They can intercept the delivery, steal your food, replace it or add something malicious. Alternatively, they can pretend to be the delivery person to break into your home.
Here, your home and the restaurant are two applications, colleagues, or customer-employee interactions. The food is the exchanged information, and the delivery person is an API, WiFi network, or system enabling the communication to happen.
In the above example, you would only realize an attack had taken place once it was too late. It makes MITM attacks difficult to detect and stop once perpetuated, as you don’t know the method, length of time, what systems, and where they’ve infected.
It puts customer data and business information at risk, such as bank or account details. So, your cyber efforts must focus on prevention to deal with this threat.
- Use communication and collaboration tools with end-to-end encryption to limit eavesdropping opportunities.
- Implement different types of testing to check for security gaps.
- Ensure access points, like WiFi networks are secure with strong passwords and encryption.
- Warn remote workers to avoid public WiFi hotspots, like in coffee shops. Provide them with VPNs to guarantee a secure environment to transfer sensitive information.
- Regularly update software and hardware to patch vulnerabilities and potential points of attack.
4. Mobile attacks
There are around 4 billion mobile internet users worldwide. Mobile devices are used for everything from social media to banking and storing sensitive information like business communications or personal information. So it’s not surprising that cybercriminals have turned their attention to smartphones and mobile devices. They can be easy targets as:
- Mobile antivirus and anti-malware security software lag behind desktop counterparts.
- People unthinkingly connect mobile devices to public WiFi networks, which can be compromised.
- There are thousands of mobile apps from official and unofficial sources which could be hidden malware.
- Multiple platforms, device types, and software makes it difficult to protect universally.
- Older devices may have outdated or vulnerable software, apps, or operating systems that can be exploited.
Mobile attacks can infiltrate the heart of your business through spyware, MITM attacks, malware, and smishing (SMS phishing). It puts your business information, sensitive customer data, and proprietary knowledge at risk. Additionally, it can be detrimental to your brand reputation, bottom line, and customer trust, leading to lost loyalty and customer churn.
In the worst cases, you may even have hefty fines or lawsuits. So, it’s critical to protect the mobile devices used in your workflow.
- Use the latest devices, security software, and updated apps.
- Only download apps from official sources.
- Provide VPNs to protect remote employees data sharing.
- Scan devices regularly for potential security threats.
- Use phishing prevention techniques to avoid smishing.
5. Internet of things
The Internet of Things (IoT) refers to everyday devices that connect and exchange data via the internet. For example, your smartphone connects to a virtual assistant like Alexa, which connects to smart TVs, lightbulbs, or temperature controls.
While this is convenient and provides a futuristic feeling, IoT devices and connections are all vulnerable to cyberattacks, such as MITM or mobile attacks. With businesses increasing their use of technology for everyday tasks, like conference room technologies, IoT can quickly turn from convenience to nightmare as threat actors leverage systems to steal data or worse.
For instance, some construction cranes use IoT for real-time monitoring and remote operation. Compromising this system could create havoc.
IoT attacks can be harder to prevent and defend due to the array of potential target points, but the following steps can help.
- Inventory IoT connected devices and systems to preempt attacks.
- Keep software and firmware updated to prevent exploits.
- Use VPNs to secure connections.
6. DDoS attacks
DDoS or Distributed-Denial-of-Service attacks happen when hackers use multiple compromised devices to overload a single target system. There are three types of attacks: application, protocol-layer, and volumetric.
For example, a volume attack might flood an ecommerce site with a massive amount of traffic. This increased traffic eats up server bandwidth and resources, leading to a server and website crash.
As a single server can host multiple sites, DDoS server attacks can paralyze numerous systems and have several unintended victims. It can be incredibly detrimental to your business operations.
For instance, companies might use Microsoft Teams Direct Routing to create a unified communications platform. However, a DDoS attack can bring down your company server or systems, leading to direct routing with Microsoft Teams not working.
It negatively impacts your communication and collaboration capabilities, halting customer service and hindering business productivity. As well as leading to a loss in revenue, your brand reputation can tarnish as customers struggle to get in touch or worry about possible data theft.
When dealing with or preventing DDoS attacks, your cyberteam should create a response squad, plan, and contingencies should your services go down. To prepare for possible threats, you must consider the attack methodology.
- Application or protocol-layer attacks can be avoided and stopped through blacklisting attacker IP addresses. Building strong firewalls and keeping your software infrastructure updated can help.
- Volumetric attacks can be prevented with firewalls and increased system capacity or cloud servers to handle manufactured traffic.
- Dedicated servers can avoid collateral damage from shared server attacks.
- Content Delivery Networks (CDNs) and server redundancy eliminate single points of failure and distribute the load, reducing the impact of increased bandwidth.
Security drives trust
The interconnected nature of modern digital devices, applications, and accounts, provides convenience for employees and businesses to boost their productivity and capability. However, cybercriminals see it as a wealth of vulnerabilities to exploit, data to steal, and organizations to disrupt.
Cyberattacks affect everyone, but businesses can feel the after-effects the most. Stolen customer and business data lead to damaged brand reputation, loss of customers, fines, lawsuits, and significant dents in revenue and growth.
So, a comprehensive cybersecurity strategy can prevent costly data breaches and downtime, strengthen business-customer relationships, drive customer conversions, and secure your business’s future.
Bio:
Jenna Bunnell – Senior Manager, Content Marketing, Dialpad
Jenna Bunnell is the Senior Manager for Content Marketing at Dialpad, an AI-incorporated cloud-hosted unified communications system that provides valuable call details for business owners and sales representatives. She is driven and passionate about communicating a brand’s design sensibility and visualizing how content can be presented in creative and comprehensive ways. She has also written great articles for PayTabs and PrettyLinks. Check out her LinkedIn profile.
How to Make Your Food Blog Irresistibly Yummy for Google Rankings?
SEO strategy is at the core of any successful blog. It is even more critical in densely populated…
0 Comments11 Minutes
How SEO Company Boosts Your Online Presence?
The web jungle is immense with hundreds and thousands of new websites cropping up every day! It is…
0 Comments6 Minutes
Keyword Research Strategies: Opportunities for SEO Success
Consider wanting to sell ice cream. You arrange your ice cream stand, but how can you tell people…
0 Comments10 Minutes
Optimizing Marketing Automation with Dynamics 365: Essential Keywords and Strategies
For organizations aiming to hold their ground and reach out to their audience effectively,…
0 Comments9 Minutes
Understanding AI, Machine Learning, and AIML: A Comprehensive Overview
We are all aware of the phrase: “Change is Constant!” It means nothing is permanent except…
0 Comments7 Minutes
What are the Cybersecurity Best Practices to Safeguard Your Digital Assets
One could say that cybersecurity is not anymore, an added luxury – it has become a necessity. Due…
0 Comments8 Minutes
8 Ways Visual Content Enhances the User Experience on Your E-commerce Website
When it comes to e-commerce, first impressions are everything. Your website is usually the first…
0 Comments7 Minutes
How to Find and Fix Orphan Pages in SEO
Orphan pages are the web pages which are not linked to any other web page of the specific site and…
0 Comments9 Minutes